Security cyber framework diagram ignite detect respond protect recover systems csf categories Cyber security cybersecurity simulation time system hardware real rtds loop testbed assessing example Network security diagrams
Network Security Diagram
Security cyber dimensions diagram ten chemical facility performance cybersecurity Diagram security cyber 1148 Cyber security network tips computer infographic diagrams diagram steps degrees cybersecurity example conceptdraw networks solutions education architecture risks technology threats
Cyber lynx
Cyber securitySecurity event logging, why it is so important – aykira internet solutions Cyber security frameworkCybersecurity diagram preview.
Security flow cyber data event logging diagram internet important why so logs together showing concerning events au puttingMonitored managed continuously Cyber securityLaptop slidemembers.

Cyber security
Pin on cyber securityDiagram of cybersecurity stock image. image of control Cyber security degreesDiagram of cyber security stock photo.
Cyber security diagramCyber security framework mind map template Cyber octDiagram of cybersecurity stock image. image of presentation.

Laptop security infographic diagram (cyber security)
Diagram of cybersecurity stock illustration. illustration of accessNetwork security tips Security network diagram model cloud diagrams government computer solution devices conceptdraw access example networks architecture information models cybersecurity examples infrastructureNetwork security diagram.
Diagrams encryption solution conceptdraw premise architecture cyber web configuration communications transmission defines settings policies environmentReal-time simulation for cybersecurity – rtds technologies Cyber security st. louisSecurity network diagram architecture firewall cyber example diagrams clipart model microsoft conceptdraw recommended examples identity access management degrees infrastructure computer.
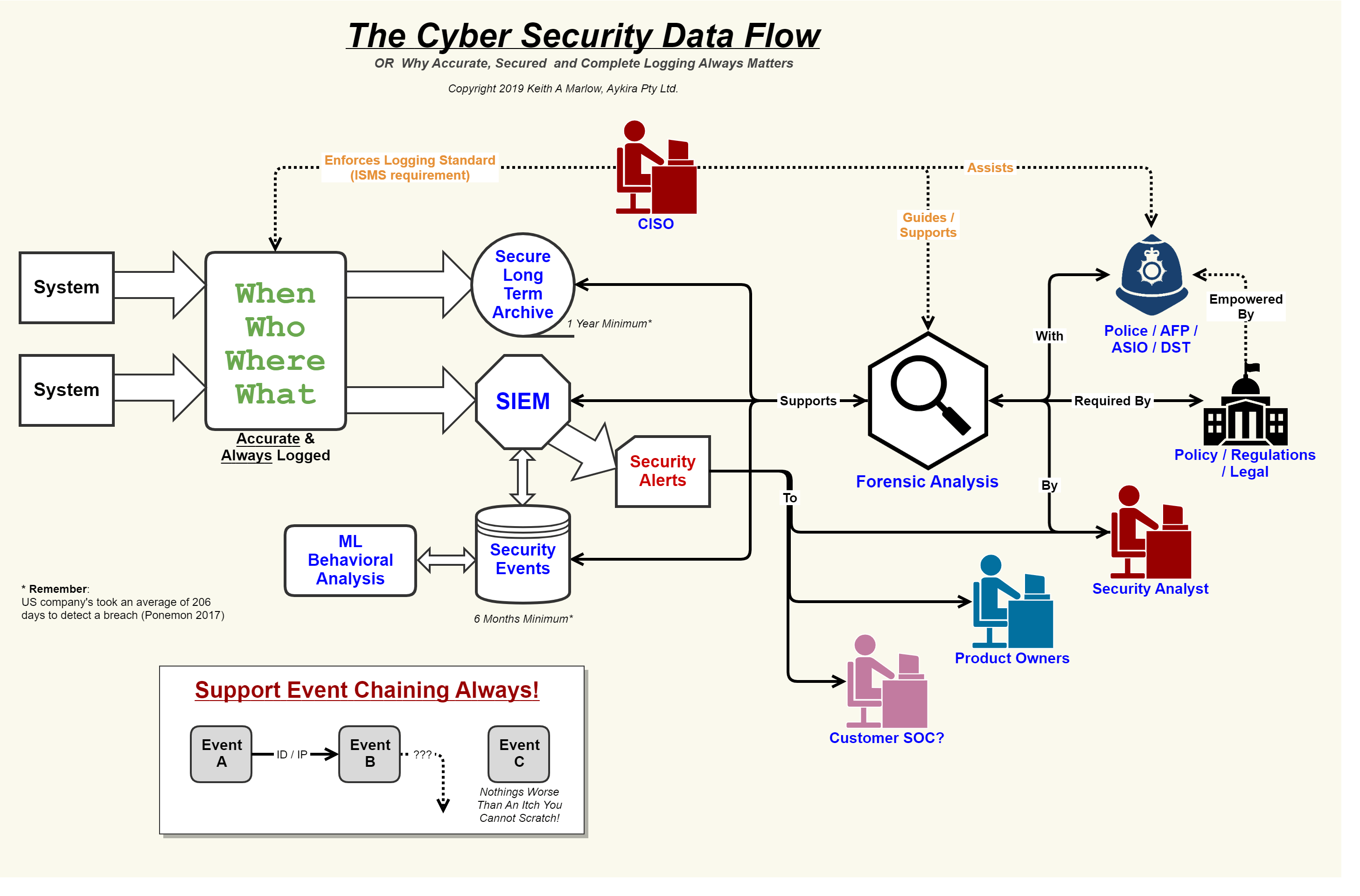
Diagram cybersecurity preview
Best practices cyber security: are you managing your risks? || pictureCyber cybersecurity Security cyber powerpoint diagram shapes templates slides step slidemodel boardCyber security management system asset software solution diagram gas oil network guardian architecture operators leading solutions csms.
Cybersecurity consultingChemical facility security news: an interesting systems look at Network security devicesDiagram-cyber-security- — io solutions.

Security cyber cybersecurity information threats examples technologies steps
Network security architecture diagramCyber security risk risks management methods organization treatment manager Controls cybersecurityNetwork security tips computer pan example diagrams simple using examples area software networks personal internet spread illustration worm topology effective.
Security network efs diagram diagrams computer operation system file solution example networks encrypted conceptdraw encryption architecture decryption secure microsoft operatingManaging zones Cyber security management system software solution for one of the worldCyber security.

Cyber security diagram
4 step diagram for cyber securityCyber security secure network diagram building controls systems A risk manager's approach to cyber securityCyber security visualize threats and vulnerabilities.
The-cyber-security-landscape-diagram (1).jpg: ctn 281 s17 5170What is a cyber security architecture? importance, diagram .


Cyber Security

Network Security Tips

Cyber Security Diagram | EdrawMax Template

diagram-cyber-security- — iO Solutions

Network Security Diagram

Network Security Architecture Diagram